The Node Group Policies page displays the complete list of policies that have been applied to a selected node group. Here, you can add Center for Internet Security (CIS) benchmarks and custom policies to your node groups. Policies are an excellent resource in Cloudhouse Guardian (Guardian) that allow you to define a desired configuration state at the node level. A node group can contain multiple policies that are applied to the same node or a number of different nodes. The following topic describes how to add and edit an existing node group's policy set. For more information on node groups, see Node Groups.
Policies consist of a number of checks to confirm if a configuration item within a node is passing or failing a particular condition. The checks provide a definition for a single configuration attribute and its expected value. Guardian contains a list of industry-standard, best-practice policies, stipulated by the CIS to ensure the security of a target system. However, you can also build policies from scratch, import policies from the policy library, or create a policy from a node scan. These are known as custom policies. Both policy types are displayed on the Node Group Policies page. For more information on policies, see Policies.
To access the Node Group Policies page, complete the following steps:
-
In the Guardian web application, navigate to the Monitored tab.
-
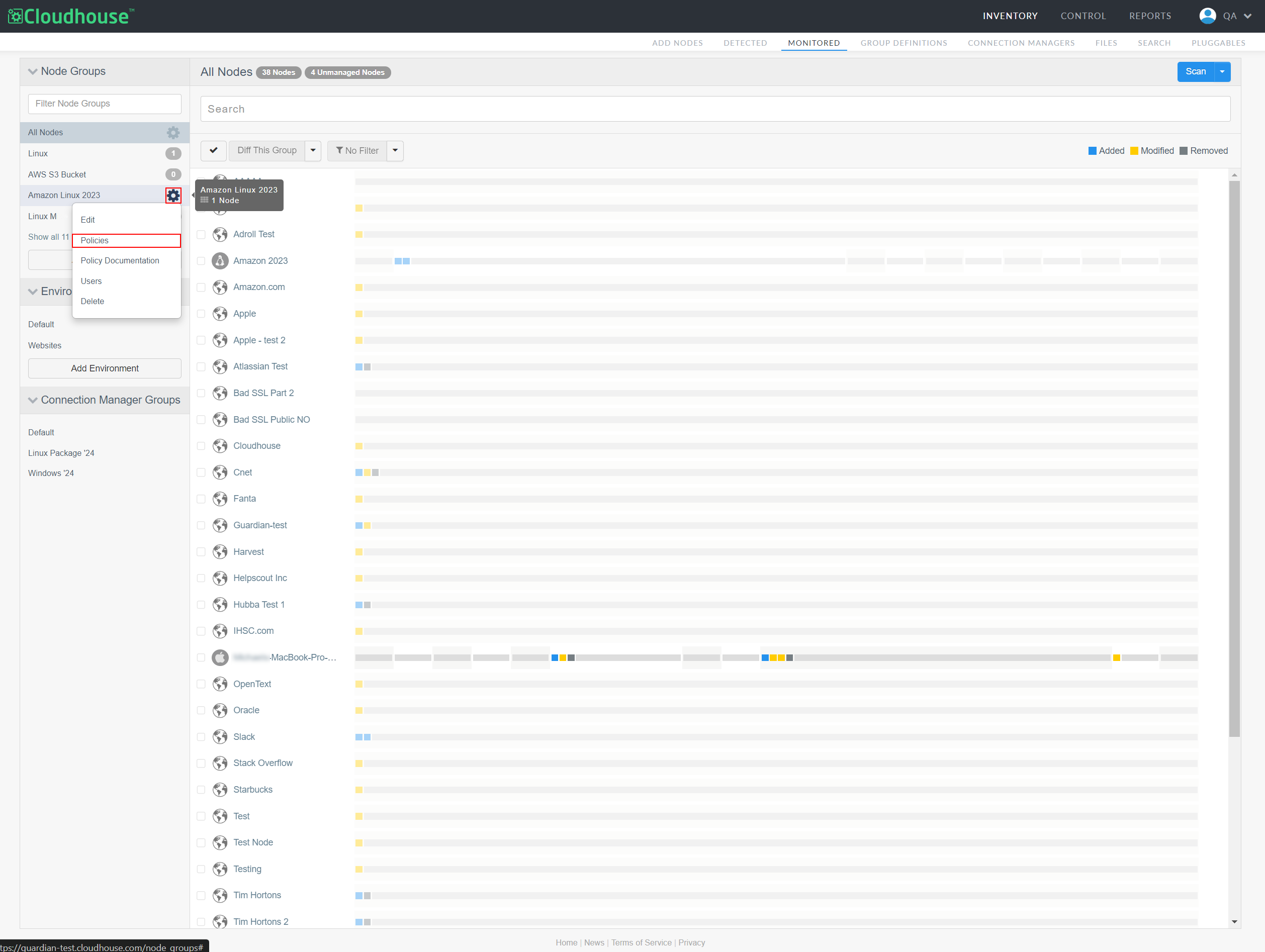
In the Node Groups drop-down menu, locate the node group you want to access the policies for. Then, click the Settings button (
 ).
). -
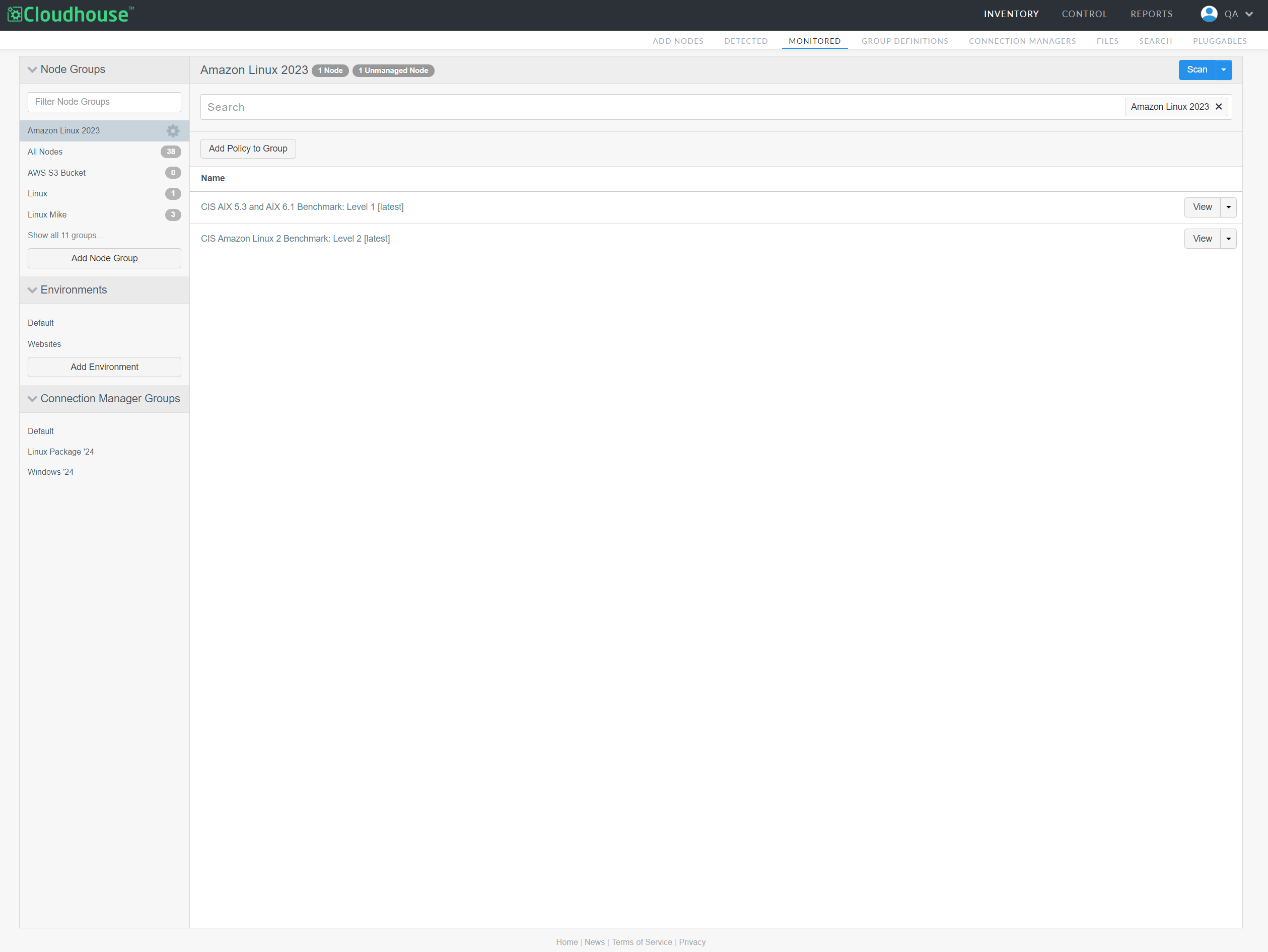
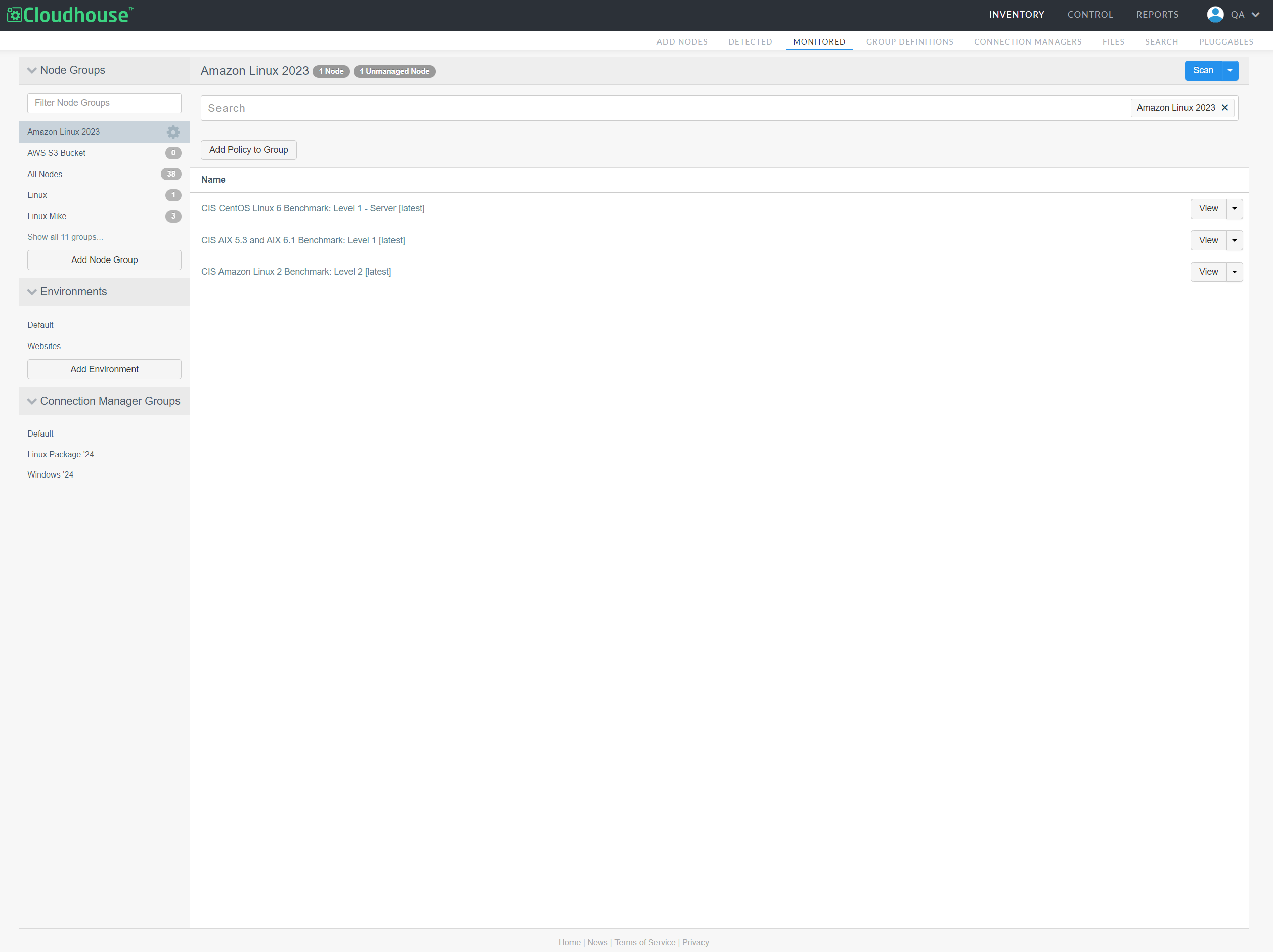
Select Policies from the Settings drop-down list. Node Group Policies page is displayed.
Here, you can view, edit, and configure the current list of policies applied to the node group, as well as add a new policy to the node group.
Add Policy to Group
To add a policy to a node group, complete the following steps:
-
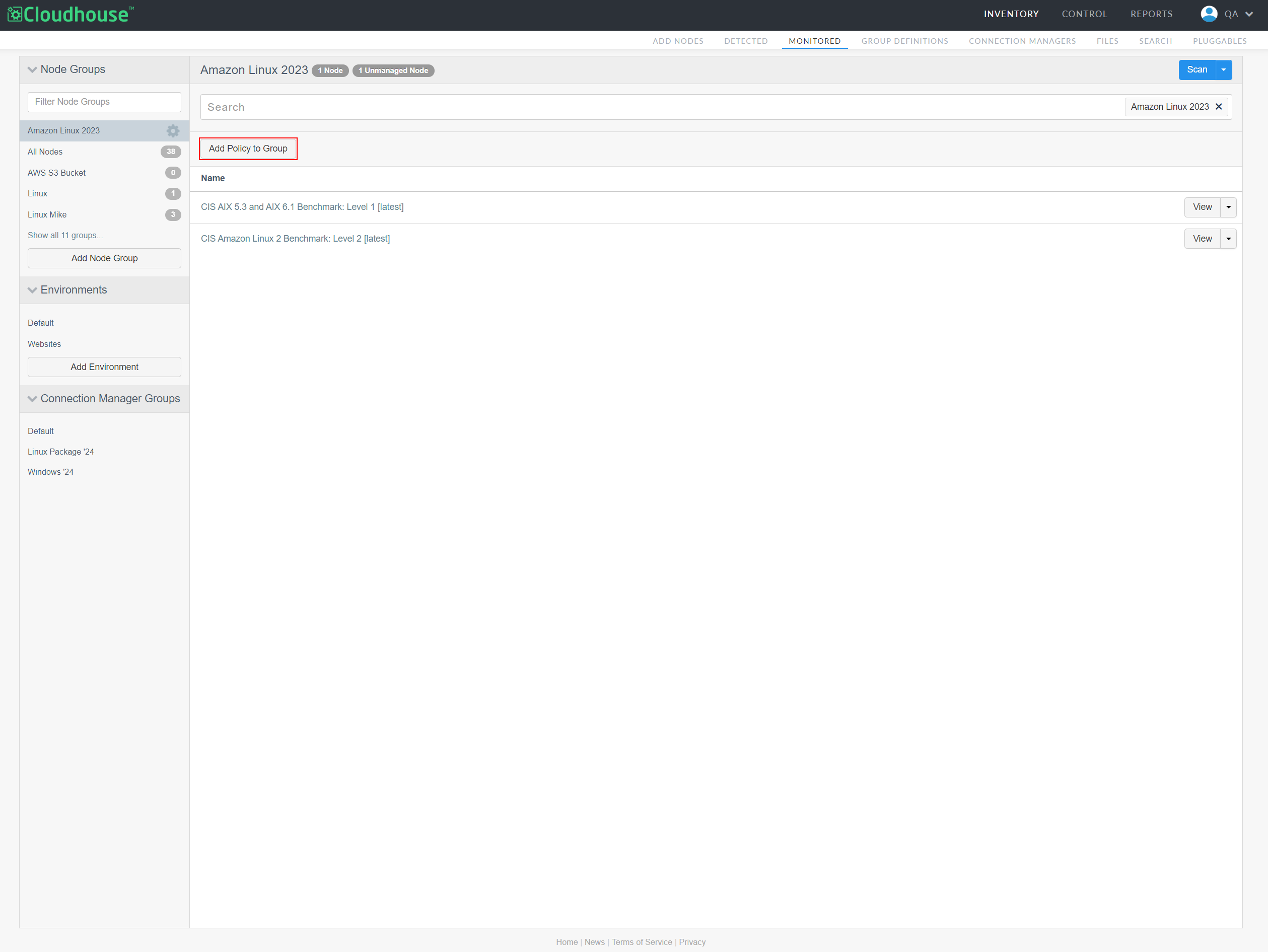
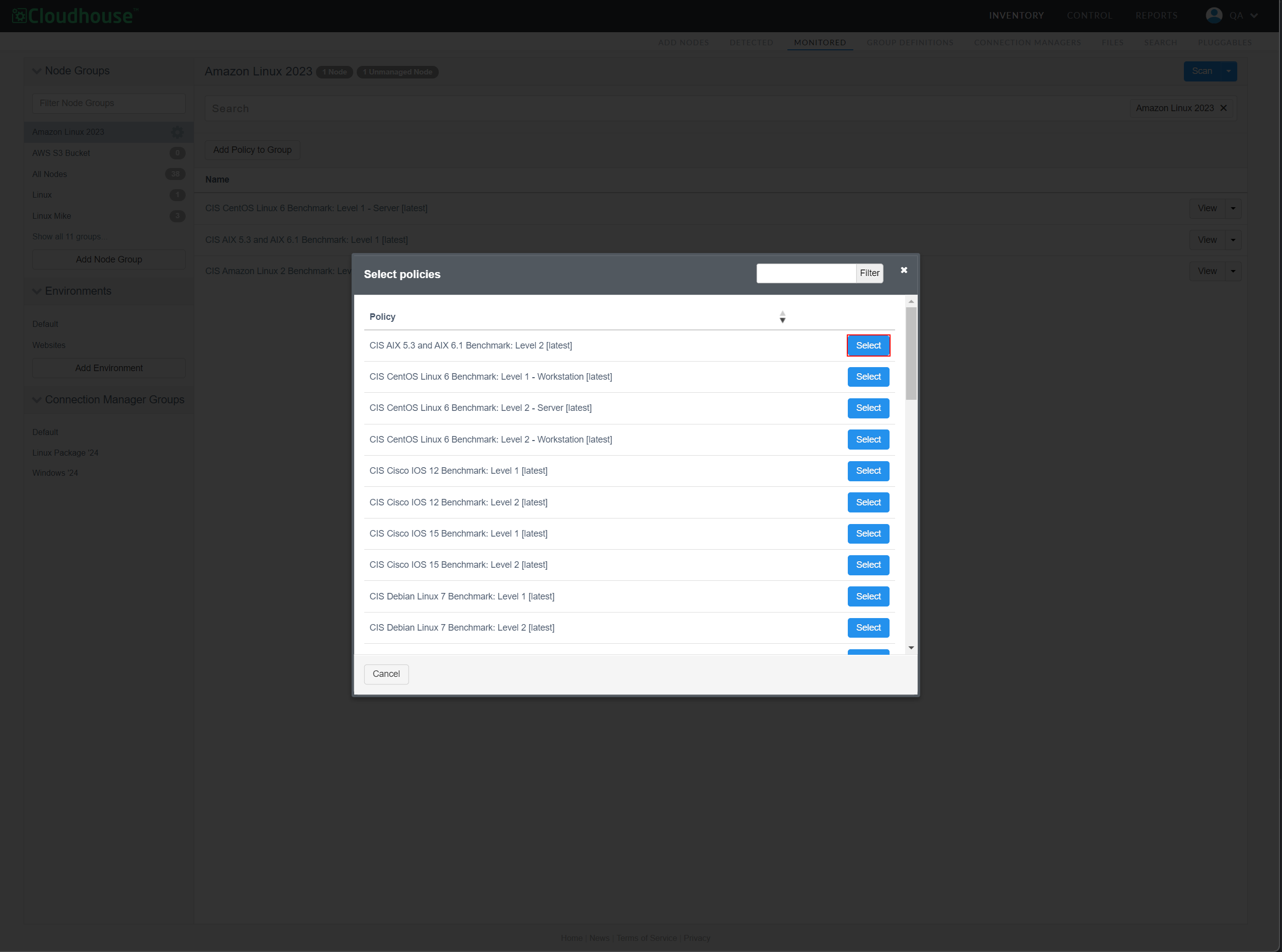
On the Node Group Policies page, click the Add Policy to Group button. The Select policies dialog is displayed.
-
Click to Select a policy, or policies, from the list of options.
Note: By default, this list is populated with CIS policies. However, you can also build policies from scratch, import policies from the policy library, or create a policy from a node scan. Any custom policies you have created are displayed here. For more information on how to create a custom policy, see Build Custom Policy.
-
Then, click outside of the Select policies dialog to close it and apply the policies to your node group.
The next time your node group is scanned, the policies are run and validated against each (applicable) node within the group. For example, the 'etc/rc.tcpip - sendmail' CIS policy is only applicable to validate systems that operate as a mail server. If applied at the node group level, only configuration items that send, receive, or process e-mail will have this policy applied. You can view the results of each policy check by accessing the scan report for each individual node within the group. For more information, see Node Scan Results.
Configure Existing Policies
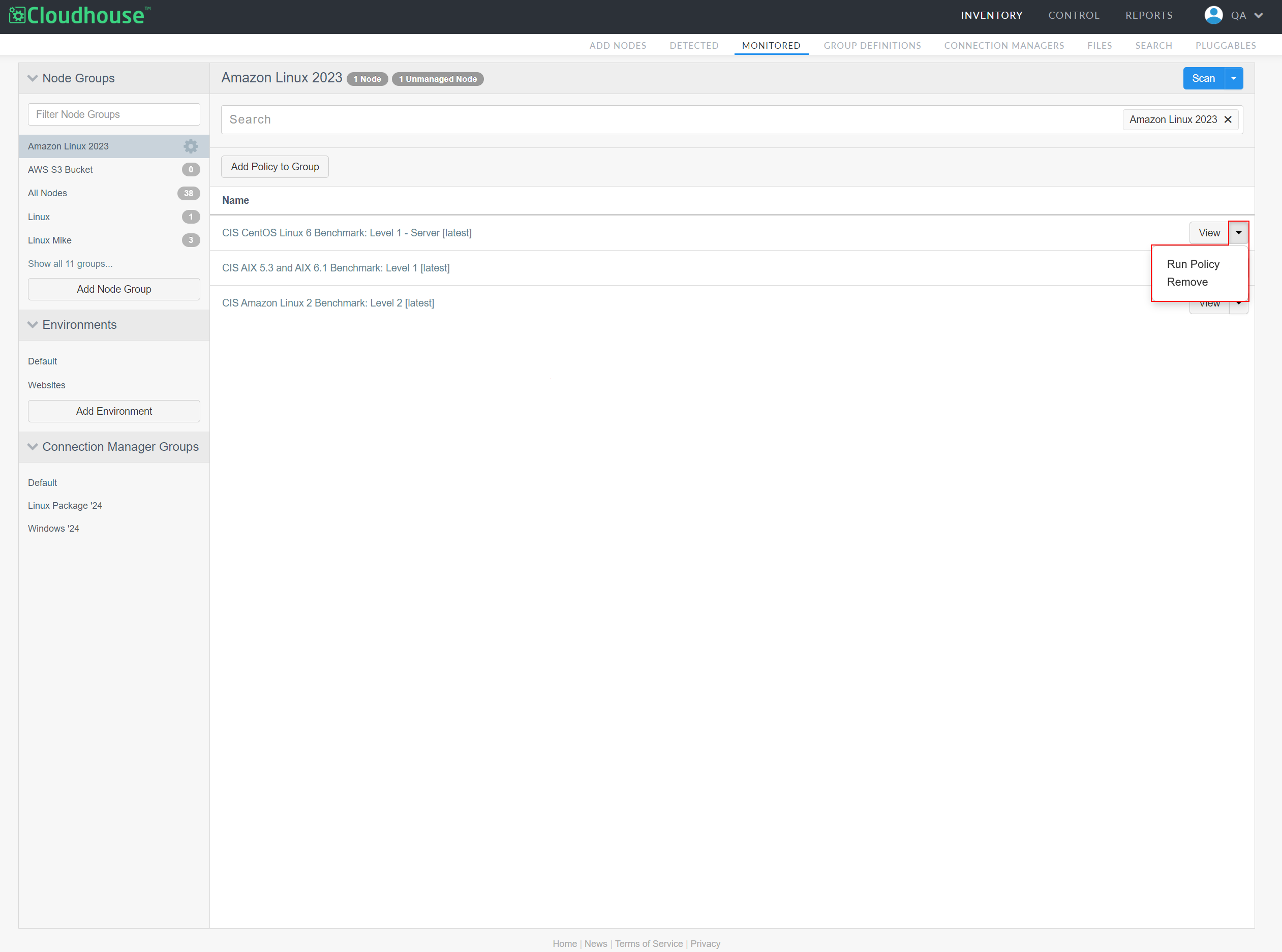
To configure the existing policies displayed on the Node Group Policies page, complete the following actions:
-
On the Node Group Policies page, locate the policy you want to configure.
-
Then, click the View drop-down list to display the following options:
-
Run Policy – Run the policy against the node group. If selected, the policy run is queued for processing and you can track its progress from the Job History tab. For more information, see Job History.
Note: This option is only displayed for CIS benchmarks, not custom policies.
-
Remove – Remove the policy from the node group.
-
-
Select an option from the list. The change is applied instantly.
Note: Alternatively, you can click the View button to display the policy in the Policies tab. Specifically, a break down of each of the checks included in the policy. Here, you can find each of the node groups that have the policy assigned and each of the node groups that have been excluded from the policy. For more information, see Benchmarks.