Access Logs
The Access Log button (
On this page, you can view information on two types of access: user logins and API calls.
Note: User logins and API calls are both considered 'User Logged In' event types in Guardian. For more information on events, see Events.
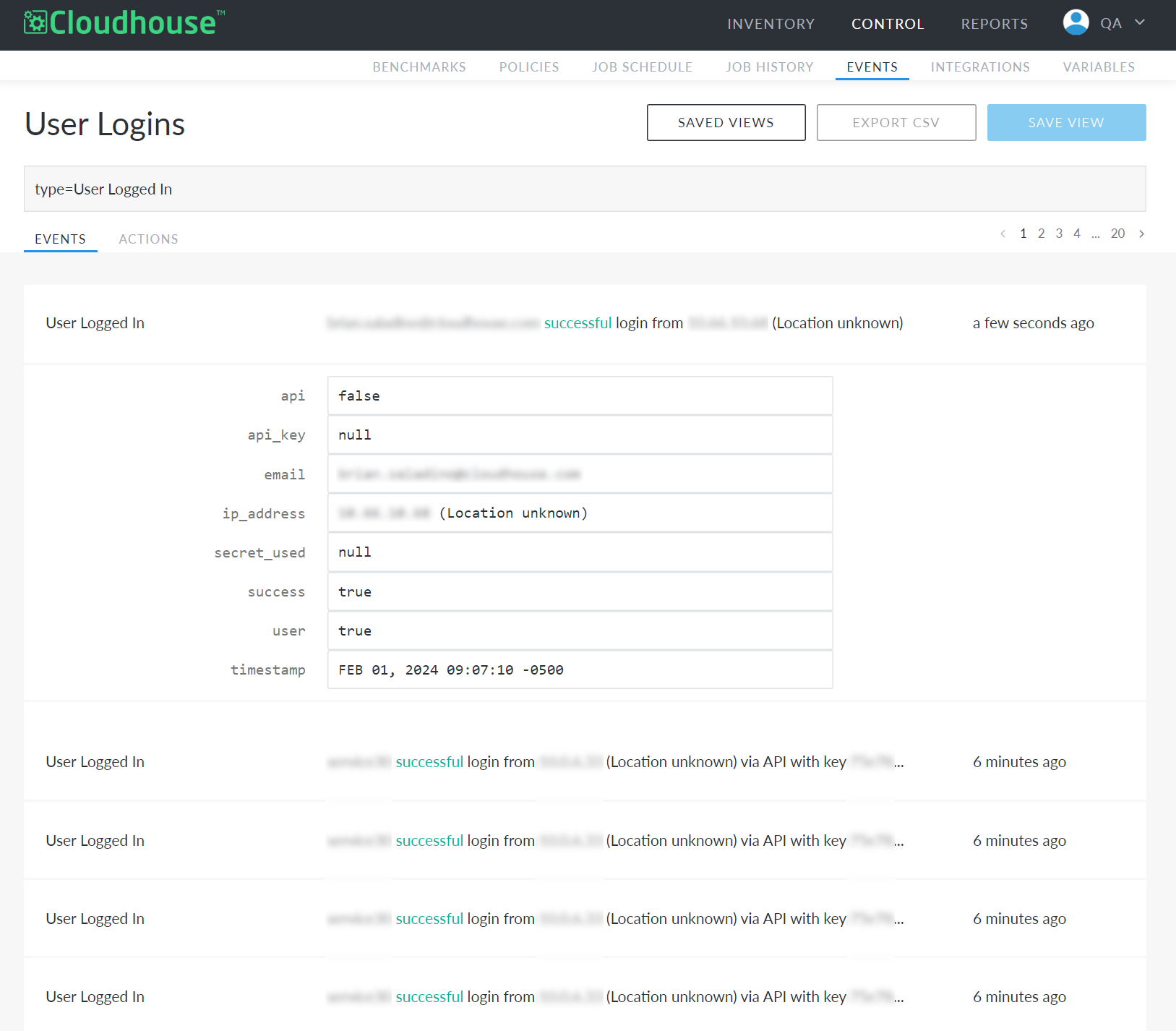
By default, the saved view for user logins page displays an overview of each access event. In the case of a user login, the user's email address and IP address are displayed, alongside the event's time stamp. In the case of an API call, the name of your Guardian organization's service account is displayed.
Note: If you have enabled the use of personal API keys in your Guardian organization, the user's personal API key is displayed here instead of the organization's service API key. For more information on personal API keys, see API Keys.
To view more information on a login event, click an item to display the following fields:
| Field | Description |
|---|---|
| API | Indicates whether the login was triggered by an API call. If 'True', the login was triggered by an API call. If 'False', the login was triggered by a user logging in to Guardian. |
| api_key |
Displays a preview of the API key used if the event was triggered by an API call. If the event was triggered by a user logging in to Guardian, 'null' is displayed. |
|
If the event was triggered by a user logging in to Guardian, the user's email is displayed. If the event was triggered by an API call, the name of the organization's service account is displayed. Note: If personal API keys are enabled, the user's email will still be displayed here even if the access event is the result of an API call. For more information on personal API keys, see API Keys. |
|
| ip_address | The IP address of the user's machine, from which access was obtained. |
| secret_used |
Indicates whether the API secret key was used. If 'True', the key was used. If 'False', the key was not used. If 'null', the access event is a user login. Read-only API calls triggered as part of scheduled jobs do not require the use of a secret key. For example, regularly scheduled node scans do not require a secret key. However, triggering a node scan using an external API call does require a secret key. |
| Success |
Indicates whether the access event was successful. If 'True', the access event was a success. If 'False', the access event was unsuccessful. False access events indicate either a failed API call or an unsuccessful user login. Note: If single sign-on (SSO) is enabled in your Guardian instance, only successful user logins are displayed as part of the User Logins saved view. With SSO enabled, user credentials are authenticated by the SSO provider. As such, unsuccessful logins are not displayed in Guardian. |
| User | Indicates whether the login was triggered by a user. If 'True', the event was triggered by a user. If 'False', the event was triggered by an API call. |
| Timestamp | The specific date, time, and time zone of the login event. |
From the Access Log page, you can also view actions configured to run upon user logins. For example, you might have an action configured to send an email letting you know when users log in to your Guardian instance. To view these actions, click the Actions tab. Here, you can also configure a new action by clicking Add Action in the top right corner. For more information on configuring actions in Guardian, see Actions.