Users
The Users page (
Note: Each organization has its own unique list of users, and one user's permissions may vary across organizations. Additionally, changes made to user permissions do not automatically apply to each organization a user has access to. For more information on organizations, see Organization Accounts.
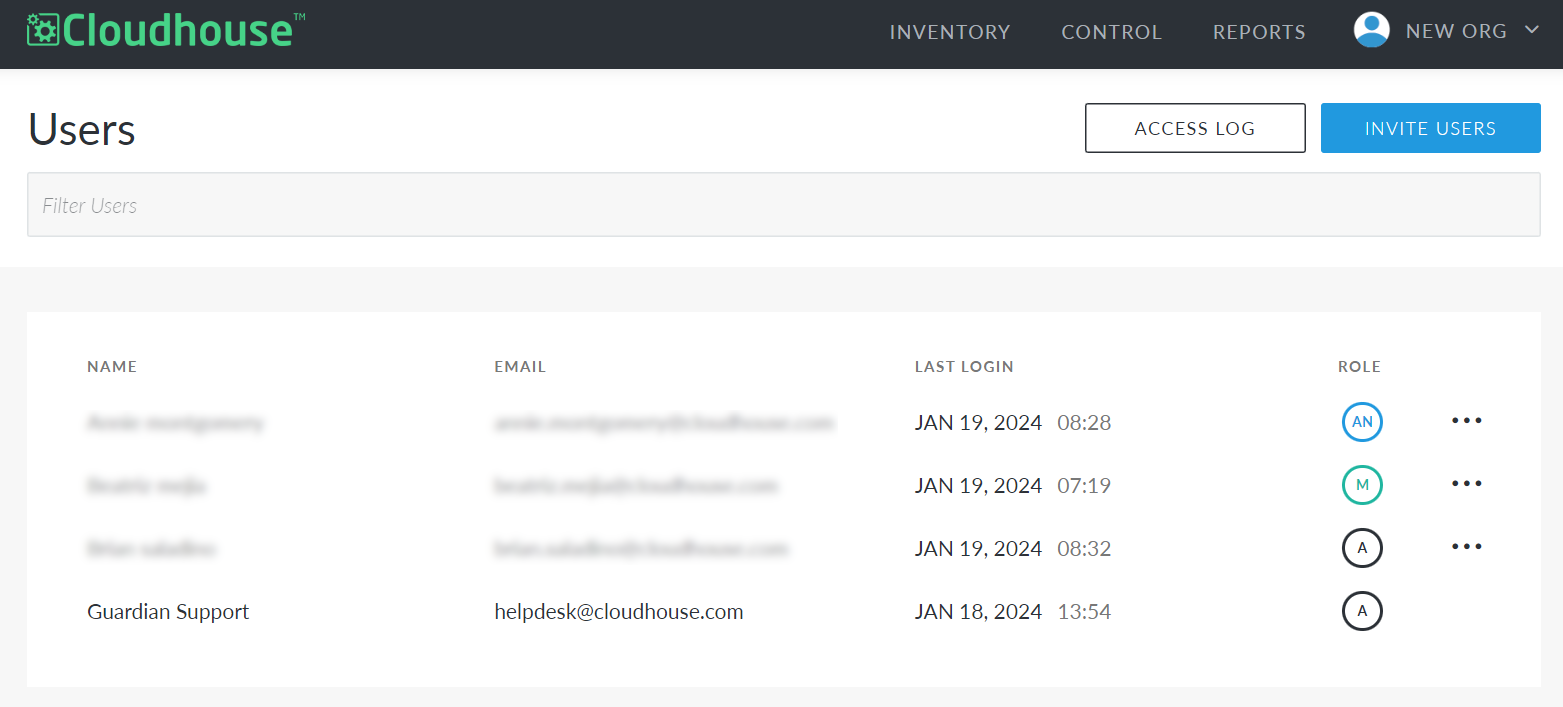
Here, a list of users with access to the current organization is displayed, alongside their Name, Email, Last Login, and Role. To find a specific user, type their name or email address in the Filter Users search bar at the top of the page. To view more information about a user, click their name to display the user account details page. For more information on user account pages, see Manage Accounts.
User Roles and Permissions
Guardian users can be assigned one of three roles. You can identify the role assigned to each user in the Role column on the Users page.
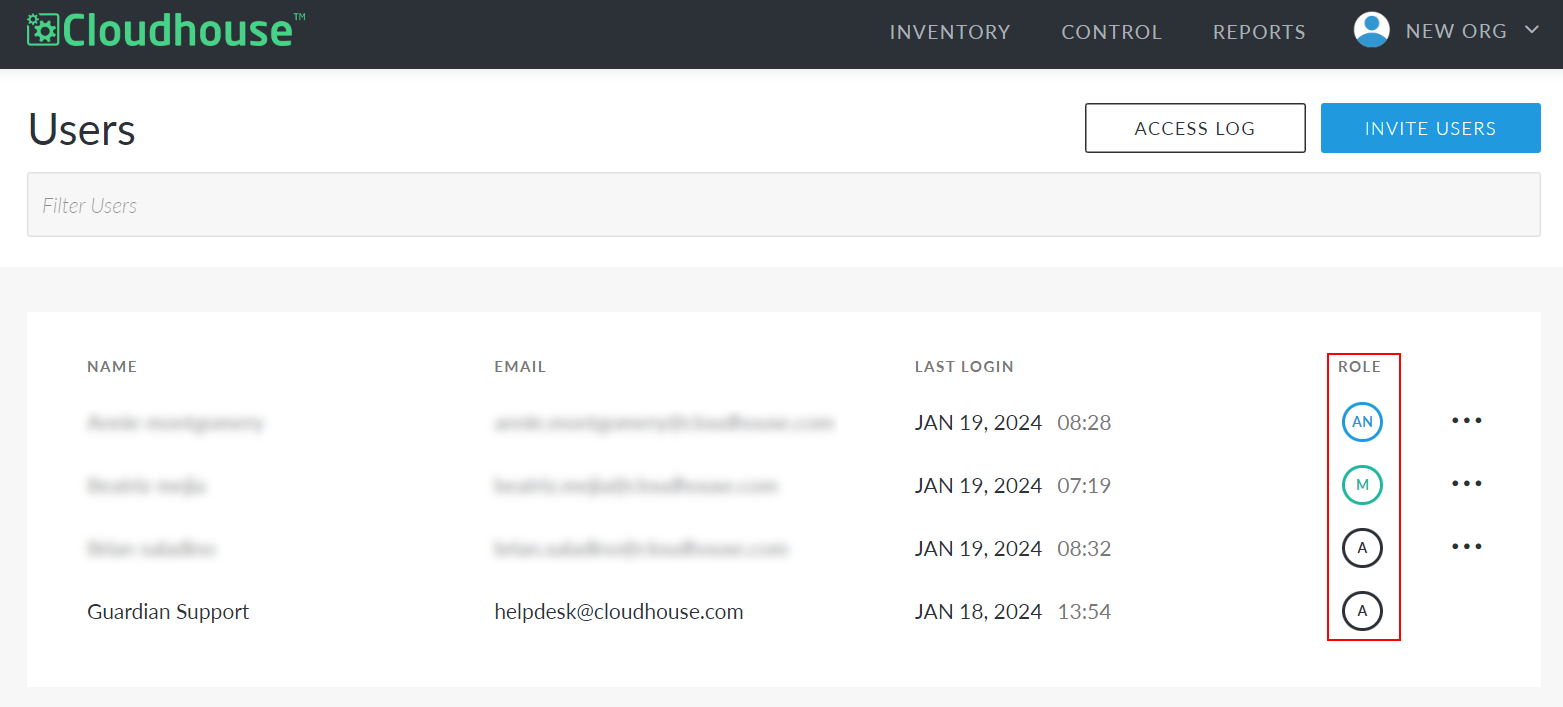
The permissions for each role are as follows:
| Role | Can Do | Cannot Do |
|---|---|---|
| Administrator (A) |
Administrators have full access to Guardian, which means they can:
|
N/A |
| Analyst (AN) |
Analysts have read-only access to Guardian, which means they can:
|
Because analysts have read-only access, they cannot:
Note: By default, analysts do not have permission to perform node scans. However, this permission can be granted at the organization level. For more information, see Organization Settings. |
| Member (M) |
Member permissions depend on the node groups the member has access to, which means they can:
For more information on adding users to node groups, see Node Group Users. |
Because member permissions depend on node group access, members cannot:
In addition to the above restrictions, members also cannot:
|
For more information on managing users in Guardian, see the following topics: